“Application security has emerged to become more important than ever as consumers are now educated enough to trade with businesses which are proactively considering the data and security of services. Thus, it works as a business enabler and trust-building factor for any web application, and especially the D2C brands,” said Venkatesh Sundar, Founder and CMO, Indusface.
Venkatesh was delivering a masterclass on ‘Application security playbook for D2C brands’ at the Brands of New India Mega Summit, YourStory’s property working towards powering India’s D2C ecosystem. Application security has turned out to be one of the major hindrances for D2C brands in embracing digitisation.
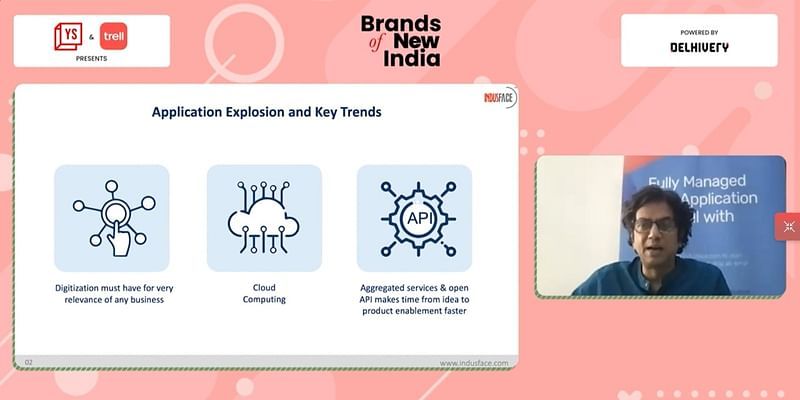
How digitisation trends changed post-pandemic
Explaining a few themes around application security, which D2C brands should follow to go digital fearlessly, Venkatesh said, “Times have changed with online orders replacing the traditional models. Thus, even the kirana store might not have a website, but is forced to adopt digitisation initiatives by partnering with either a delivery channel or an e-commerce portal, creating a web storefront for them.”.
The website thus formed can be stated as an application solving a particular problem, or perhaps a better way of doing business.
Another emerging trend records both the new-age and traditional businesses shifting to cloud computing, essentially for speed, convenience, and decreasing cost. “While businesses can dedicate time to their core activities, the cloud computing explosion is happening with several new applications, increasing the speed of work in less time,” he added.
“In the entire ecosystem, an aggregation of various independent services – starting from the payment gateway, to shopping cart product, or product catalogues – are placed together, enabling businesses to have a proper D2C product for their customers. Thus, aggregated services through the open API of those services being exposed, is reducing the time from conception of the idea to it being a product made for consumption,” said Venkatesh.
The number of applications, combined with cloud computing, open API, and aggregation of services, have resulted in a multiplier effect in terms of speed of deployment to the number of applications.
Challenges of application security
Businesses are always held responsible for the security of the application, even if the core developer is someone else. The public cloud providers might discuss shared responsibilities and wish to be held responsible for network securities, but in reality, the ownership lies with the business.
While ensuring a unified approach to the consumers, there are several moving parts including services hosted by the third-party application systems like payment getaways, checking out, shopping carts, etc, each with its own developmental and innovative cycle. As the business is responsible for the security of the entire system, building it involves both risk and specialised expertise.
“D2C is all about speed and innovation, the touchpoint being the customers. Partnering with a specialised third-party, who again is a part of the ecosystem, helps to solve the issue,” added Venkatesh.
Of course, the threats are real, and all the applications are vulnerable to cyber attacks. “Even if a few moving parts get exposed, it increases the risk of threats. Once a threat has occurred, it takes a hacker to send in a certain kind of payload on the framework, if the business has not already taken measures to fix it,” he explained.
How to address these challenges?
“Having a razor-sharp focus on risks from your application stack, being provided as a service to your customers under your ownership, also helps to start it simple,” said Venkatesh while stressing the importance of a playbook and execution plan.
Once the brands/businesses have details of the inventory of the applications and publicly consumable touchpoints, they need to think ahead and anticipate the areas from which risks might evolve. “Here, insist on doing a program on security risk assessment continuously, even extending to the reports on applications your business has integrated with. Businesses should also have a web protection mechanism, based on the risk detection that would work as an ultimate intelligent gathering mechanism for a hack attempt,” he added.
The next part of the execution plan is based on the partner ecosystem that businesses/brands tend to create in India. Thus, now the plan remains to partner with vendors who would provide risk management, risk assessment, and risk protection, continuously as the security threats are dynamic, and it’s important to keep up with the changing scenario.
Now, comes the last bit of the plan, which Venkatesh describes as the biggest in terms of the culture built by the organisations, especially in the D2C domain, where the trust factor plays a major role. Some of the major catastrophes in terms of hacks and exploits that have occurred are not owing to the business's inabilities in handling those breaches, but the inability to communicate transparently and acknowledge the problem. The entire communication program around a breach that happens needs to be done transparently, and this should work as an effective habit every time. “Be open in sharing the findings and actions taken with all the stakeholders, including your customers, and this works in trust-building,” said Venkatesh.
Security application is central to building trust, according to Venkatesh, and is as important as mitigating risk. “It’s best to partner with the best minds for security issues without trying to do everything by yourself. Allow yourself to grow fruitfully, and let your customers be delighted,” he said.
You can watch videos from all the sessions of Brands of New India Mega Summit here. Don't forget to tag #BrandsOfNewIndia when you share your experience, learnings, and favourite moments from the event on social media.
For information on future events, collaborations, and information regarding the D2C ecosystem, please visit our website.
